Rubber Ducky - Arduino UNO Configuration for Arduino UNO Board: Download and install the Latest version of Arduino ( Recommended : Linux/Mac) Download Boot-loader Sketch(INO) from reference URL Open the INO file in the Arduino IDE Connect a Plain(no other wire connection) Arduino UNO to Laptop via USB cable In Arduino IDE, Select Tools->Board->Arduino/Genuino UNO In Arduino IDE, Select Tools->Port->ttyACM0 [Yours could be different. Use dmesg command to identify] Verify and Upload the Code Wait for the message “Upload Done” and Disconnect the USB cable Make the cable connection as per the below screenshot attached Connect the USB cable again back to laptop and the boot loader will install by itself Wait for 1 to 2 min till the boot-loader get installed Disconnect USB cable from the laptop and disconnect all the jump wire and make the board plain Configuration for Arduino IDE: Connect the Board to laptop via USB cable Nav...
Popular posts from this blog
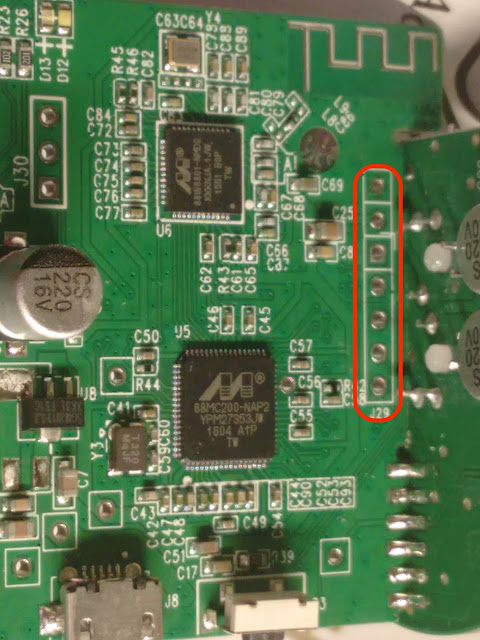
JTAG PIN Identification
My Setup Parrot Linux Arduino UNO Broadlink RM Mini Software Arduino IDE JTAGEnum ( https://github.com/cyphunk/JTAGenum ) JTAG PINS to be Identified TCK - Test Clock TMS - Test Mode TDI - Test Data IN TDO - Test Data Out GND - Ground Hardware Connection Set up Connect Laptop and Arduino (USB cable) Arduino Digital PIN (any 5 pins) to RM Mini (5 pins) [Except 1 - VCC and 1 - GND] Note: If you are using JTAGENUM, the JTAGenum sketch uses the DIGITAL PIN from 2 to 11. Refer the line number 72(ino file) Software Connection Set up Download the INO sketch from the github Open the Arduino IDE and Load the downloaded JTAGEnum sketch Choose the correct Serial Port and Board Compile and Upload the sketch Open the Serial Monitor Set the correct baud rate Enter the command to scan ("s") Arduino PIN Layout Digital PIN 2(Black) Digital PIN 3(Whi...
Android Exposed Service Exploit
Android Application Service Code(Application 1): ------------------------------------------------------------------------------------------------------------ Details ------------------------------------------------------------------------------------------------------------ Package Name: com.example_service Class Name: Server_Service AIDL Interface Name: service_interface ------------------------------------------------------------------------------------------------------------ Code: Server_Service.java ------------------------------------------------------------------------------------------------------------ package com.example_service; import android.app.Service; import android.content.Intent; import android.os.IBinder; import android.os.RemoteException; public class Server_Service extends Service { public Server_Service() { } //Create new stub and write implementation for all the function declared in the AIDL file...

Comments
Post a Comment