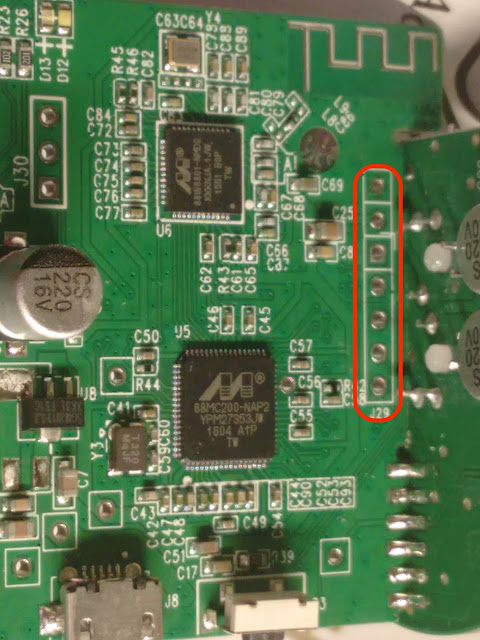
Rubber Ducky - Arduino UNO Configuration for Arduino UNO Board: Download and install the Latest version of Arduino ( Recommended : Linux/Mac) Download Boot-loader Sketch(INO) from reference URL Open the INO file in the Arduino IDE Connect a Plain(no other wire connection) Arduino UNO to Laptop via USB cable In Arduino IDE, Select Tools->Board->Arduino/Genuino UNO In Arduino IDE, Select Tools->Port->ttyACM0 [Yours could be different. Use dmesg command to identify] Verify and Upload the Code Wait for the message “Upload Done” and Disconnect the USB cable Make the cable connection as per the below screenshot attached Connect the USB cable again back to laptop and the boot loader will install by itself Wait for 1 to 2 min till the boot-loader get installed Disconnect USB cable from the laptop and disconnect all the jump wire and make the board plain Configuration for Arduino IDE: Connect the Board to laptop via USB cable Navigate File->Pref