DNS Spoofing
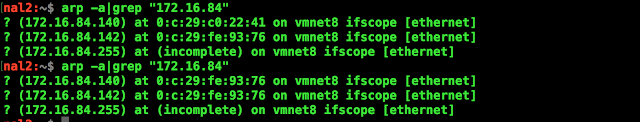
Setup Gateway => 172.16.84.2 KALI => 172.16.84.140 [Victim] PARROT => 172.16.84.143 [Attacker] Attacks ARP Spoofing [Using Scapy] DNS Spoofing [Using Ettercap DNS_Spoof Plugin] Attack Flow Attacker perform ARP spoofing [to redirect all the traffic from victim system to attacker machine] Attacker perform DNS Spoofing [to steal the data by phishing/sniffing] Scapy ARP Spoof Packets spkali => Poison the kali cache table spgate => Posion the gateway Refer ARP Spoofing by Scapy https://just2secure.blogspot.ae/2017/02/arp-poison.html Ettercap DNS Spoof Configuration root:~$ nano /etc/ettercap/etter.conf Change 1 (Change the value to Zero) ec_uid = 0 # nobody is the default ec_gid = 0 # nobody is the default Change 2 (uncomment the 2 lines) redir_com...